Keylogger And A Good Binder
Jan 4, 2018 - Hacking Software to Hide Trojans and Viruses. Binder is a software used to bind or combine two or more files into one file under one. Hack Facebook Password using Keylogger. I’ve included screenshots in these instructions to help demonstrate how to create your Facebook hacker keylogger. First of all download the Keylogger and a good binder.
Whats a Binder? Binder is a software used to bind or combine two or more files in one file under one name and extension. The files to be binded can have any extension or icon. The user has choice to select the name, icon and various attributes of binded file. If binded file contains an application (in our case - RAT or keylogger), the application is also run when the actual binded file is run.thus Binder is used to for the following things • To Hide Files (Key loggers, Rats, Viruses ) • To Bypass antivirus detection. Binder Software's - Free Download Binder Software's Provided here are 100% clean, All the Binders here are password protected so please download the password file also Note:- Usually binder software's are detected as virus, So please turn off your Av's(antivirus software ) Before using them 1.
Flaming Binder.
Hack a Facebook password using a keylogger involves the following steps: 1. Create your server that will hack passwords. Extract the icons from any software 3.
Bind the Keylogger to make it hidden 4. Spread your keylogger to victims Note: This tutorial is for Educational Purposes only. Sudalleyblog is not responsible for any misuse of knowledge. Let’s start this Facebook hacking tutorial in detail: STEP 1: Create Server for Hacking Passwords First of all, for hacking any Facebook account password, we have to create our keylogger server that will run on the victim’s machine, capturing his keystrokes and emailing us the record.  The keylogger server building process consists of several steps: 1.
The keylogger server building process consists of several steps: 1.
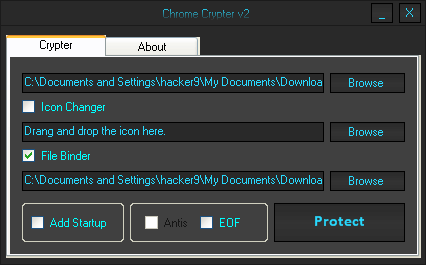
First of all download the Keylogger and a good binder. Binders are easily available via a Google search. Extract the RAR file. Now you will get one folder and three files as shown in the below snapshot: 3. Open the Keylogger file. Here you will need a gmail ID and password. For safer use, create a fake Gmail account and use it as shown below: 4.
Click on server settings as shown. Here, enter the time at which you want to receive reports; it’s always preferable to use a 20 minute timer for receiving files. Click on the Output box to choose the location of the file and give it a name. We recommend using a system process name to make it undetectable, like svchost, or check any process name from your task manager and name it. Other fields are optional. The complete snapshot is shown below: Second step to choose time interval and name of output file 5.
Click on Log and Result Setting. In Log Email Title enter the subject of email like “my keylogger report” or anything else that you you like. Click the last two options that add computer name and add the victim’s name. The snapshot is shown below: Hack Facebook account password using Keylogger 6. Now click on “Other Options.” In this section you just have to do one thing. Most hackers prefer warning message POP up, but I prefer keylogger using any message – so unclick the message button.
When you bind it with any other software it should not have a warning message attached, otherwise it will be detectable. Finally click on Build Keylogger.
You will see your keylogger file at the location that you have chosen in the 4th step. This keylogger server file will be used to bind with other software in Binding Step.
Now your keylogger server is ready for you to hack Facebook accounts. Step 2: Extracting the icon file from any installer (resource hacker) 1.
Open the resource hacker folder and select the reshacker file. Go to its menu and open any setup file. Suppose we want to attach our keylogger to a Ccleaner setup file.
Open the Ccleaner setup with resource hacker. In the menu, there is one action button. Click on it and then click save all resources. Resource Hacker to Extract the Icon files from software’s 4. Save all the resources to the desktop or any other location of your choice.